Cloud storage presents many advantages to organizations – it is in many cases cheaper and more reliable, offloading the overhead of maintaining servers and other infrastructure costs onto the provider compared to storing your data on-premise. At the same time, this advantage comes with an unfortunate potential for lapses in security, as demonstrated by the most recently publicized leaks from Microsoft.

What are the advantages of Cloud storage?
The advantages of Cloud storage have been thoroughly discussed in the past few years as the Cloud went from strength to strength. In short, the main positives are in lowering incurred costs and increasing accessibility.
Cloud infrastructure is all handled by a Cloud provider, who hosts different clients on their servers and maintains their function. In this way, companies can completely offload their overhead and maintenance fees onto a third party without losing any storage space or computing power.
At the same time, the same Cloud solution has an ancillary advantage – increased accessibility from anywhere in the world. By definition, Cloud solutions are off-prem and require connectivity to external systems. This has lead to an unimaginable productivity boost by allowing various forms of remote work and constant uninterrupted access to company data.
Why use on-prem storage?
The main advantage of on-prem storage is complete direct control over your data. While this comes at the potential cost of stifling productivity, it helps prevent some avenues of leakage. A good example of why this is important came to light this week, with Microsoft disclosing a 38TB data leak.
The leak came through a an excessively permissive Shared Access Signature (SAS) token, which allowed full control over the shared files. Shared Access Signature (SAS) tokens are intended to provide businesses with a means of granting access to resources within your storage account.
“Due to a lack of monitoring and governance, SAS tokens pose a security risk, and their usage should be as limited as possible. These tokens are very hard to track, as Microsoft does not provide a centralized way to manage them within the Azure portal,” Wiz warns. “In addition, these tokens can be configured to last effectively forever, with no upper limit on their expiry time. Therefore, using Account SAS tokens for external sharing is unsafe and should be avoided.”
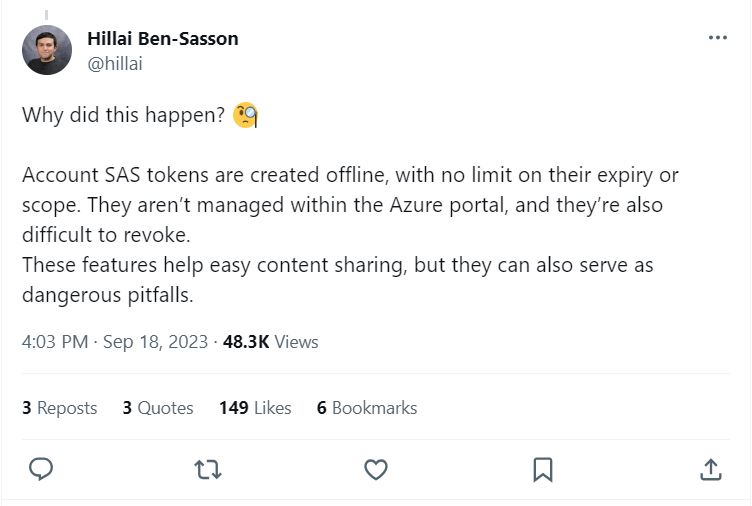
Source: https://x.com/hillai/status/1703771680798040479?s=20
In an advisory on Monday by the Microsoft Security Response Center (MSRC) team, Microsoft said that no customer data was exposed and that the leak was also contained to one particular department. However, it stands as a clear example of how user error combined with the easy sharing options on a Cloud solution can expose your data to risk.
Keep your data secure
The balance between keeping your data secure and maintaining accessibility and productivity is a difficult one to strike. Organizations have to make decisions regarding where they intend to make sacrifices. Fortunately, there are tools to make this decision easier.
TECH-ARROW’s contentACCESS archive and backup solution gives organizations options, including the possibility of storing their data locally on-prem, on a Cloud solution, or as a hybrid of the two. Data placed in contentACCESS remains accessible for reference and further use, but also remains securely stored away from potential deletion, corruption or leaks. A well-implemented archive and backup is key to keeping your business continuity intact and your critical information safe.
Interested in learning more? Contact us! Our team of experts is ready and waiting to discuss your business’ needs and how TECH-ARROW can best meet them.
Take the best steps to protect your data – with TECH-ARROW.
Archive all your O365 data with contentACCESS